Cybercriminals can Exploit Keyboard Acoustics to Crack Passwords
Passwords have long been identified as a glaring weak point in cybersecurity, plagued by several issues including widespread password reuse and the tendency for individuals to choose easily guessable passwords to avoid memorization challenges. Despite efforts to maintain strong password hygiene, even the most meticulously crafted passwords can end up compromised following a data breach
The emergence of acoustic attacks represents a significant cybersecurity threat, highlighting the inadequacies of traditional username and password authentication methods. These attacks capitalize on the sound emitted by keystrokes to extract sensitive information, serving as a stark reminder of the insufficiency of relying solely on passwords to safeguard our digital systems.
Researchers have been actively exploring various techniques to illicitly obtain sensitive information by analyzing keystrokes. The integration of artificial intelligence (AI) has notably enhanced the accuracy of identifying keystrokes. However, challenges persist due to environmental factors and background noise, leading to inconsistencies in the results of these analyses.
What is Acoustic Attack?
Acoustic attacks exploit the sounds emitted by computing devices to extract sensitive information. Unlike conventional software exploits, side-channel attacks derive data from indirect clues such as timing, power usage, or emitted sounds. Acoustic attacks specifically involve analyzing these sounds to uncover confidential data like passwords or PINs.
Although acoustic attacks have been known for some time, their complexity has grown substantially in recent years, driven by advancements in microphone technology and machine learning. Previously, executing such attacks required specialized equipment and expertise, constraining their prevalence and impact.
Recent research on Acoustic Attacks
The IACS E26 resolution talks about “Cyber resilience of ships” which is to be effective on 1st January 2024, with the aim to establish minimum requirements for the cyber resilience of ships, to provide technical guidance to stakeholders, and create more resilient ships to cyber-attacks. The resolution focuses on the ship, not individual systems, or components, and is meant to be used in conjunction with other industry standards and regulations.
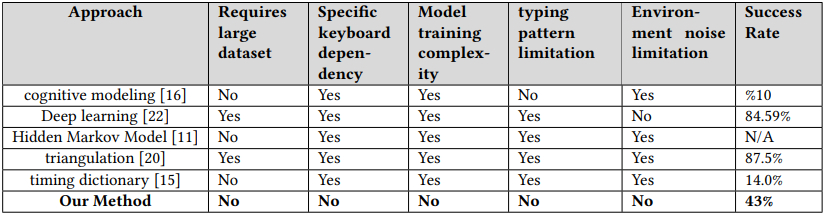
Various keylogging models comparison table (arxiv.org)
Despite its average success rate of 43%, which may appear lower than that of previous methods, the developed approach presents notable advantages. Unlike earlier techniques, this method does not require controlled recording conditions or dependence on a specific typing platform. This heightened flexibility makes it more applicable for real-world attacks. Furthermore, by leveraging specific target-related parameters, the technique can generate adequate and reliable data to decipher a target's overall input through post-capture analysis.
Performing the acoustic attack
The technical paper authored by researchers Alireza Taheritajar and Reza Rahaeimehr offers a comprehensive exploration of their acoustic side-channel method.
A critical component of their approach involves gathering typing samples from the target to correlate specific keystrokes and words with corresponding sound waves. While the dataset encompasses typing samples acquired under diverse conditions, capturing multiple typing sessions is deemed essential for the success of the attack. Notably, the researchers emphasize that the dataset need not be excessively large to yield effective results.
Furthermore, the paper elaborates on various potential methods for capturing text, including avenues such as malware infiltration, malicious websites, browser extensions, compromised applications, cross-site scripting, or compromised USB keyboards. Each of these avenues represents potential entry points for acquiring the necessary typing samples to facilitate the acoustic side-channel attack.
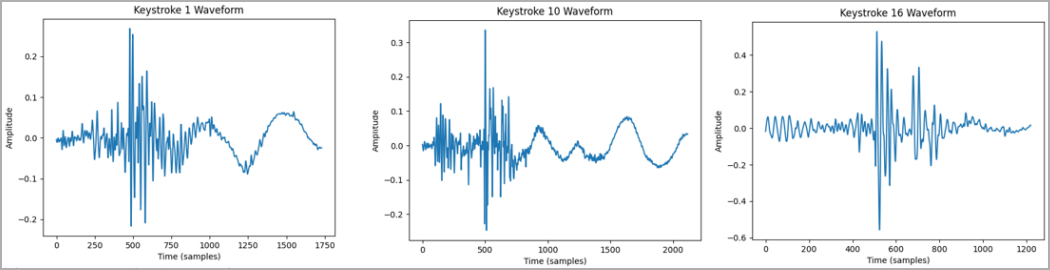
Extracted keystroke waveforms (arxiv.org)
The attack capitalizes on the unique sound emissions produced by different keystrokes and the distinctive typing patterns of users, captured through specialized software to compile a dataset.
To record the target's typing, a concealed microphone may be placed in close proximity or compromised devices nearby, such as smartphones, laptops, or smart speakers, can be utilized remotely.
The method predicts typed text by analyzing audio recordings of keyboard activity, with accuracy bolstered through filtering predictions using an English dictionary.
What sets this approach apart from others is its ability to achieve a typing prediction accuracy of 43% (on average) even under the following challenging conditions:
- Recordings contain environmental noise
- Recorded typing sessions for the same target occurred on different keyboard models
- Recordings were made using a low-quality microphone
- The target employs any typing style freely
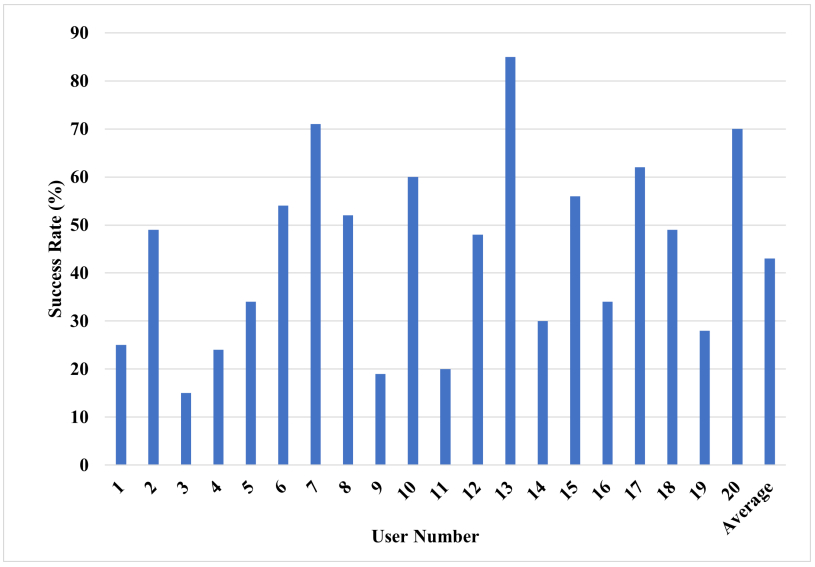
Test subjects’ overall success rate (arxiv.org)
Possible Mitigations
For users concerned about potential acoustic side-channel attacks, the paper suggests several strategies to enhance security.
One approach is to vary typing styles or employ randomized passwords, making it more challenging for attackers to deduce patterns from keystroke sounds. Additionally, users can consider utilizing software designed to replicate keystroke sounds, white noise generators, or software-based filters to obscure audio signatures.
The study found that the attack model remained highly effective even with very quiet keyboards, indicating that adding sound dampeners to mechanical keyboards or switching to membrane-based keyboards may not provide significant protection.
Implementing biometric authentication where possible and utilizing password managers to automate input of sensitive information can further mitigate risks associated with manual entry of passwords. These measures collectively contribute to strengthening defenses against acoustic side-channel attacks.
REFERENCE
- New acoustic attack determines keystrokes from typing patterns By Bill Toulas - BleepingComputer
- New acoustic attack steals data from keystrokes with 95% accuracy By Bill Toulas - BleepingComputer
- Your Keyboard Might Be Betraying You: Acoustic Attacks & Passwordless Prevention By Jacob Frehn - Portnox
About the Author
Ruben George
