Double-Blind Password strategy: Additional Security Layer
Passwords are an essential aspect of our digital lives, serving as the first line of defence against unauthorized access to protect our personal information, online accounts, and digital identities. The importance of strong passwords has never been more critical. By creating unique and robust passwords, we fortify the walls of our virtual fortresses, safeguarding our sensitive data from potential threats.
In this era of heightened cybersecurity concerns, best-practice for secure password is constantly being challenged. Password managers have aided users to stay up to date with any compromises and recommends better password for increased security encryption. But as proven with the recent incident with LastPass, a popular password manager, getting compromised and exposing classified data of LastPass users, that password managers aren’t safe from withstanding cyber-attacks. This comes down to the point on what is the next best effective standard for secure password.
The basic idea behind a double-blind password strategy is to prevent the service provider from gaining access to the user's actual password. This is achieved through a simple method of splitting the passphrase into two seperate keys. One half of the key is stored in the password manager while the other half is kept away.
What is a Double-Blind Password Strategy and when should it be used?
A double-blind password strategy, also known as "horcruxing", "password splitting", or "partial passwords", is an approach to password management that involves storing the long and complex part of a password in a password manager and keeping the short unique identifier, such as a PIN code or word, to yourself.
To log into a service or website, use the password manager to fill in the complex part and add the easy-to-remember unique identifier. Most people can easily remember a short PIN code or word but struggle with longer passwords.
For example, say your short phrase is kcx7. You would store your complex, randomly generated passwords in your password manager and use them as follows.
- • eQ7U$YRC!G becomes eQ7U$YRC!Gkcx7
- • 4yRVZbS8%n becomes 4yRVZbS8%nkcx7
- • $C!bVuSU2f becomes $C!bVuSU2fkcx7
Splitting the password into two separate key phrases makes it difficult for attackers to gain full access should the attackers compromise your password manager. even if the service provider's systems are compromised, an attacker would not be able to obtain the user's actual password. This is because the master password is never transmitted or stored on the service provider's side.
Limitations of using Double-Blind Password Strategy
While passwords have been a widely used method for authentication and securing digital accounts, they do have several limitations. Security measures can vary across platforms and websites. For instance, some websites may only allow short passwords.
When using the minimum 12-character password length as recommended by NIST 800-63B guideline along with an additional key phrase, such as “apple”, to the end of the password increases the password length to 16-characters which might not be compatible to some password limits.
With the double-blind password strategy, it is important to ensure that your password manager only auto-fills, as submitting the form without the unique identifier will fail. This may sacrifice some usability for security. This method may only work for some environments and are adopted by users. If an organization uses a password manager, splitting the password may not be effective if a shared vault is being used—as the identifier will have to also be broadly shared manually.
Avoiding Common Password Mistakes
The double-blind password strategy can not always work based on how it is created. A user can still create an insecure password or use one that has already been compromised. Increased computing power means that even random passwords with various characters are more susceptible to cracking.
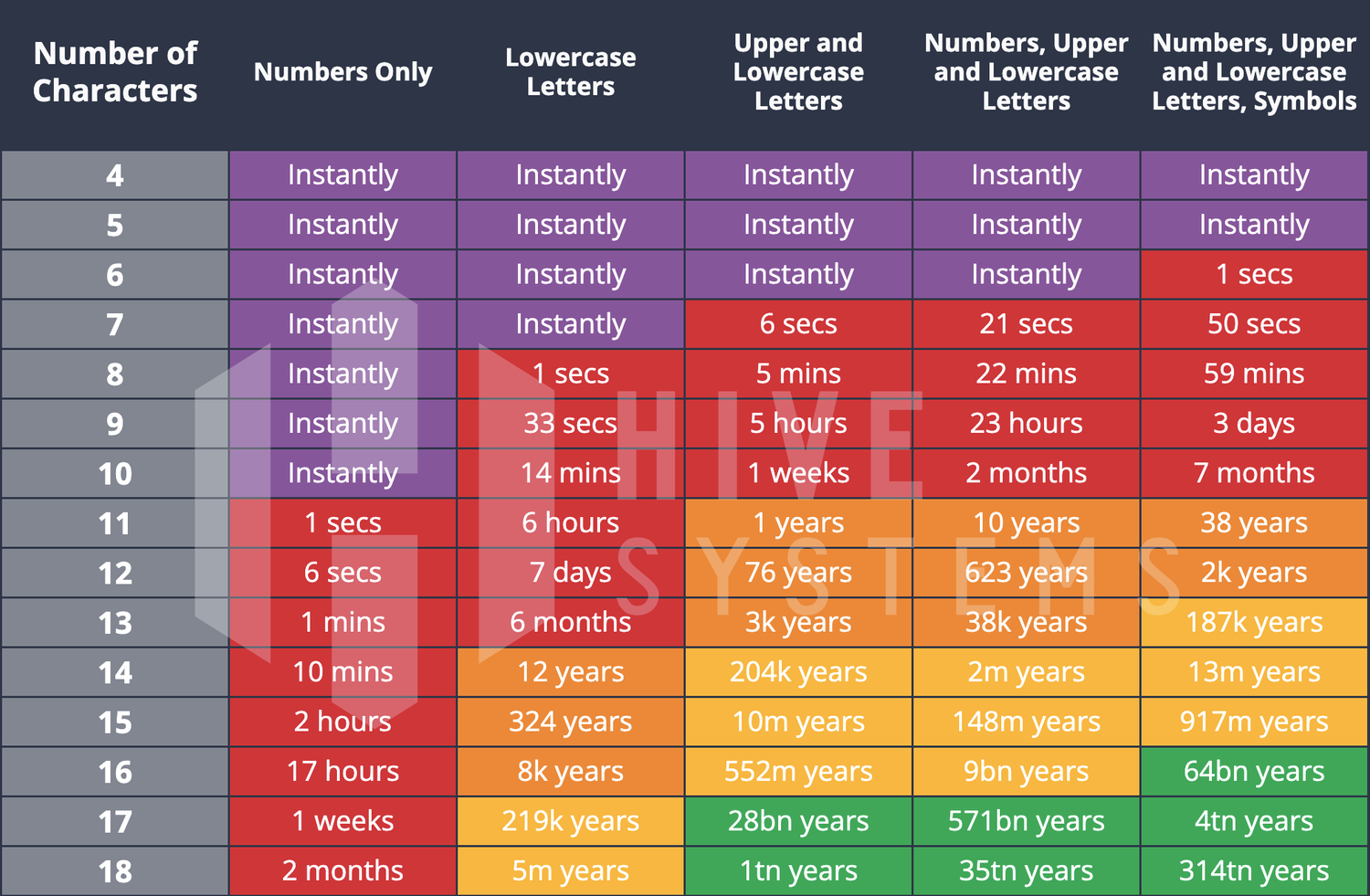
The following table shows approximate times it would take an attacker with a modest amount of hardware and modern software to crack MD5 passwords of various length and complexity. Attacker or group of attackers that have more resources would be able to accelerate these times with investments in additional hardware capacity. With ransomware pay out reaching million-dollar levels, the additional setup expense can be seen as easily worth it.
Any of the following common errors may result in a password that leave your organization open to password vulnerabilities:
- • Using short and simple passwords, such as repeated sequences, common words, or phrases that are easily able to be cracked.
- • Failing to change a password after a breach can be a major problem. This is especially true in scenarios where the unique identifier, known only to the user, could be compromised by potential threat actors.
- • Failing to use multi-factor authentication (MFA) can leave you vulnerable to token stealing or phishing attempts.
Reference
Following article originally written by SpecOps Software prepared for Bleeping Computers.
- What’s a Double-Blind Password Strategy and When Should It Be Used By SpecOps Software for Bleeping Computers
- How Safe is your Password? By Constellation Cyber Consultancy
About the Author
Ruben George