What is Digital Risk?
In the digital era, the world is becoming increasingly interconnected and reliant on technology. With the rapid advancement of technology, we are seeing an explosion of digital data, which is growing at an unprecedented pace. This digital revolution has brought with it a range of new opportunities, but also new risks.
Digital risk refers to the risks associated with the use of digital technology, including the risks to the security, privacy, and integrity of digital data. As individuals, businesses, and governments rely more heavily on digital platforms, the risks associated with these platforms increase manifold. These risks encompass a wide array of threats, including data breaches, identity theft, financial fraud, cyberattacks on critical infrastructure, and much more.
When a company grows, its attack surface widens, making it more vulnerable to online dangers. As a result, digital risk is an inevitable side effect of technological innovation and digital transformation. Fortunately, techniques for reducing digital risk have been established, allowing businesses to scale their operations with confidence.
Cybersecurity Risks
Cybersecurity risks are one of the most significant digital risks. Cybercriminals are constantly looking for vulnerabilities in networks, software, and hardware to exploit. The consequences of a cyber-attack can be catastrophic, including data breaches, theft of sensitive information, financial loss, and damage to reputation.
To mitigate cybersecurity risks, individuals and organizations should implement robust security measures, such as firewalls, antivirus software, and intrusion detection systems. They should also regularly update software and ensure that passwords are strong and changed frequently.
Privacy Risks
Privacy risks are another major digital risk. With the amount of data being collected and stored by companies and organizations, the risk of privacy breaches has increased significantly. Personal data, such as name, address, and phone number, can be used for identity theft or sold to third-party organizations for marketing purposes.
To protect privacy, individuals should be careful about the information they share online and ensure that their privacy settings are set appropriately on social media platforms. Organizations should also implement data protection policies and procedures, including encryption and access controls.
Reputational Risks
Reputational risks are also a significant concern in the digital world. Social media and online review sites have given individuals and organizations a platform to share their opinions and experiences with a wide audience. This can be positive, but it can also be negative
Negative reviews or comments can damage an individual or organization's reputation, resulting in financial loss and loss of trust from customers or clients. To mitigate reputational risks, individuals and organizations should monitor their online presence, respond quickly to negative feedback, and be transparent in their communication.
What is Digital Risk Management?
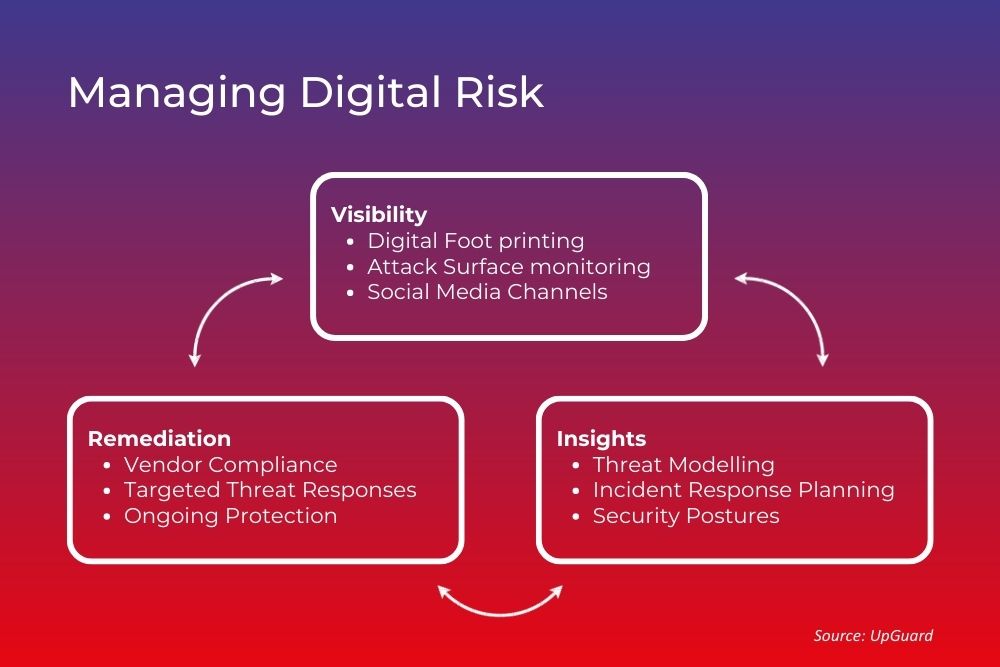
Digital risk management refers to digital processes for improving the evaluation and monitoring of risk—which may include cybersecurity risk, third-party risk, operational risk, and numerous other types of risk. These risks can impact the organization’s financial performance, operation, or reputation.
A digital risk management solution can include the use of process automation, decision automation, digitized monitoring, and early warning systems, and it can provide in-depth analytics to help your organization better monitor your compliance status and current threat level for all risk factors.
The following steps outline a digital risk management framework with a specific focus on mitigating cybersecurity and data leak risks:
Step 1. Identify all Exposed Assets
Identify all assets exposed to potential unauthorized access. This should include all social media channels and resources housing sensitive data. A digital footprint can be mapped with the assistance of an attack surface monitoring solution.
Critical assets at risk of exposure can include:
- • Social media channels
- • Cloud platforms
- • Shadow IT
- • Critical data (customer data, employee data, health information, financial information, etc.)
Step 2. Monitor for Data Leaks
A data leak detection solution can discover any data leaks linked to your organization to provide both visibility and vulnerability insights into this commonly overlooked attack vector.
Cybercriminals are always searching for data leaks to arm their data breach campaigns. By remediating data leaks before cybercriminals discover them, cybersecurity, and therefore all other categories of digital risk, will be protected.
Step 3. Keep Risk and Threat Models Updated
With a digital footprint established, all threat intelligence data can be collected to create a model of your threat landscape. In addition, to improve cyber resiliency, organizations should also consider reviewing their incident response, business continuity, and disaster recovery plan to ensure all security teams can respond to all potential cyber risk factors.
Businesses should also update these cyber resiliency plans every time their threat model is refreshed. Best practices suggest that these security policies are reviewed consistently, on at least an annual basis.
Step 4. Secure Access to All Exposed Resources
To protect against reputational damage, privileged accounts and digital assets should be protected from compromise. Rather than only focusing on established cyber defences around sensitive resources, detection parameters should be broadened to detect and block all unauthorized network access.
This also involves access control for internal usage as well. Controlled privileges allow organizations to prevent unauthorized employees from accessing critical data beyond their job roles, reducing the risk of insider threats as well.
Strategically placed honeytokens will alert organizations to any unauthorized access attempt. Further access to resources can be mitigated with a Zero Trust Architecture (ZTA), an assume breach mentality and enhanced Privileged Access Management (PAM) security.
Step 5. Keep Vendors Compliant
The risk of non-compliance has both a financial and cybersecurity impact. Non-compliance is linked to poor security efforts, and regulatory fines could range from $14 million to $40 million.
To mitigate the risk of non-compliance, it's not enough to only monitor the internal ecosystems, the entire vendor network needs to be purged of security vulnerabilities. Organizations need to perform their vendor due diligence to ensure that all new and existing third parties in the supply chain are properly evaluated and assessed.
Cybercriminals could breach your organization through vendors with poor security postures. A third-party risk management solution will ensure all vendors remain compliant through regulatory-specific risk assessments.
Conclusion
In conclusion, digital risk is a significant challenge in the digital world. Cybersecurity, privacy, reputational, and compliance risks are just some of the major risks that individuals and organizations face. To effectively manage digital risk, individuals and organizations should implement robust security measures, protect privacy, monitor their online presence, and ensure compliance with legal and regulatory requirements. Digital risk management is an ongoing process that requires collaboration, investment, and a commitment to safeguarding digital assets, privacy, and operations in an interconnected world.
About the Author
Ruben George