
Air-Gapped Computers vulnerable to data theft through power supply radiation
Security researcher Mordechai Guri from Ben-Gurion University developed a new form of cyber-attack named COVID-bit that uses electromagnetic waves to transmit data from computers isolated from the internet over a distance of at least two meters, which can be captured using a receiver. A nearby smartphone or laptop can act as the receiver and can be able to capture information from the isolated device through the walls.
Prior works of Guri includes “ETHERLED” that can be able to capture information from air-gapped systems using the LEDs of network card, and “SATAn” which is capable of capturing data from air-gapped systems using SATA cable Wi-Fi antennas.
About air-gapped devices.
Physical air-gapped devices are one of the many security measures that involves isolating computers and preventing it from establishing an external connection of any type. These computers are physically separated from any form of connection wirelessly or physically with other computers or network devices. Air-gapped systems are commonly used in critical infrastructures such as government, power plants, weapon controllers and many more that are isolated from the public network for security measures.
Typically for an attacker to gain access to these air-gapped devices, it requires attackers to “cross the air gap” and physically sit down in front of the computer to compromise it. Attackers can also gain access to these computers with the help of a rogue insider that can place a custom-made USB with a purposeful designed malware into the target computer and plant the malware to make it possible to access.
How COVID-bit works.
COVID-bit attack can be used to transmit data from air-gapped computers using the power supplies. The researcher demonstrates by injecting a malware program that regulates the CPU load and core frequency in a particular manner that forces the power supply to emanate electromagnetic radiation on a low-frequency band within 0-48 kHz. Guri explains that “the primary source of electromagnetic radiations in switched-mode power supply (SMPS) is due to their internal design and switching characteristics”. With the conversion from AC-DC to DC-DC, the switching components turning on and off at specific frequencies can create a square wave.
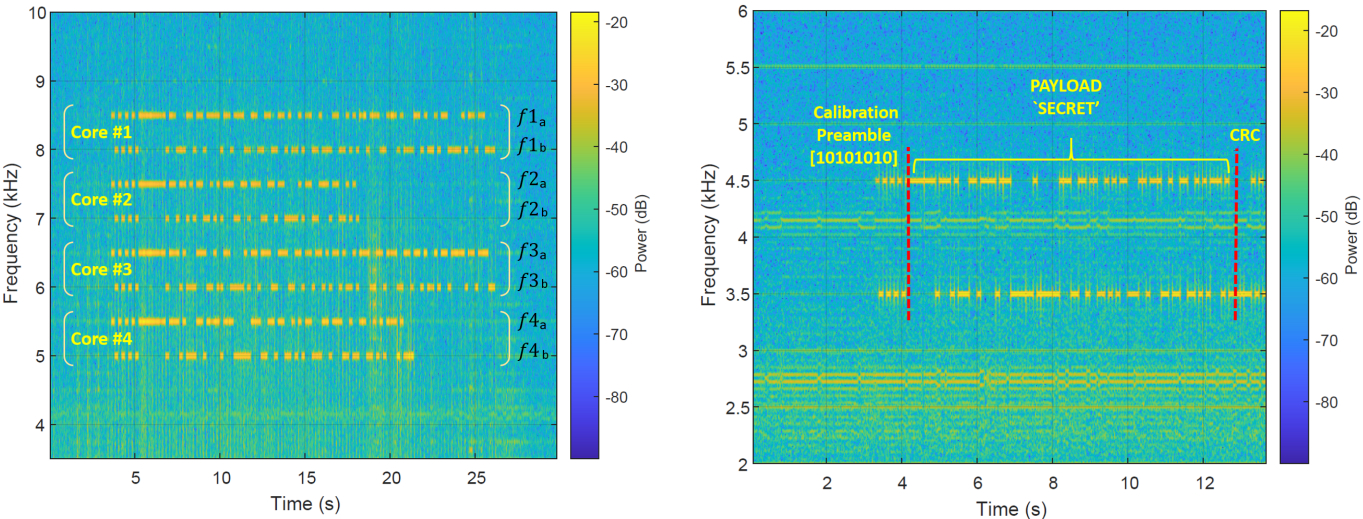
The electromagnetic wave can carry a payload of raw data, following a strain of eight bits that signify the beginning of the transmission. The receiver can be a laptop or smartphone using a small loop antenna connected to the 3.5mm audio jack, which can be easily spoofed in the form of headphones/earphones. The smartphone can capture the transmission, apply a noise reduction filter, demodulate the raw data, and eventually decode the secret.

Guri tested three desktop PCs, a laptop, and a single-board computer (Raspberry Pi 3) for various bit rates, maintaining zero-bit error rate for up to 200 bps on PCs and the Raspberry Pi and up to 100 bps for the laptop.
Laptops perform worse because their energy-saving profiles and more energy-efficient CPU cores result in their PSUs not generating strong enough signals. The desktop PCs could reach a 500bps transmission rate for a bit error rate between 0.01% and 0.8% and 1,000 bps for a still acceptable bit error rate of up to 1.78%. The distance from the machine was limited for the Raspberry Pi due to its weak power supply, while the signal-to-noise ratio was also worse for the laptop as the testing probes moved further away.
The researcher stated that the maximum tested transmission rate (1,000 bps), a 10KB file would be transmitted in 80 seconds, a 4096-bit RSA encryption key could be transmitted in as little as 4 seconds or as much as ten minutes, and the raw data from one hour of keylogging would be sent to the receiver in 20 seconds.
A detailed explanation of the conducted research can be viewed by CLICKING HERE. The paper further talks about the conducted research, types of tools used to conduct this experiment and a detailed explanation of the end results from the research.
Protection against COVID-bit
The best defense against the COVID-bit attack is to tightly restrict access to the air-gapped device that can prevent the device from being installed with the malicious content. This is something to consider preventing the device from being accessed through an insider threat.
Further prevention is recommended by monitoring CPU usage and detecting for any suspicious pattern that doesn’t match the computer’s expected behavior. This countermeasure will not be accurate as there are high chances of receiving false positive. The overhead data processing running, it will reduce the performance of the air-gapped device and increase energy consumption. Another possible countermeasure is by locking the CPU core to a specific frequency, which will make it exponentially harder to generate the data-carrying signal. This method has the drawback of reduced processor performance or high energy waste, depending on the selected lock frequency.
The following article refers heavily to the original content created by Bill Toulas of BleepingComputer from December 10, 2022
About the Author
Ruben George
